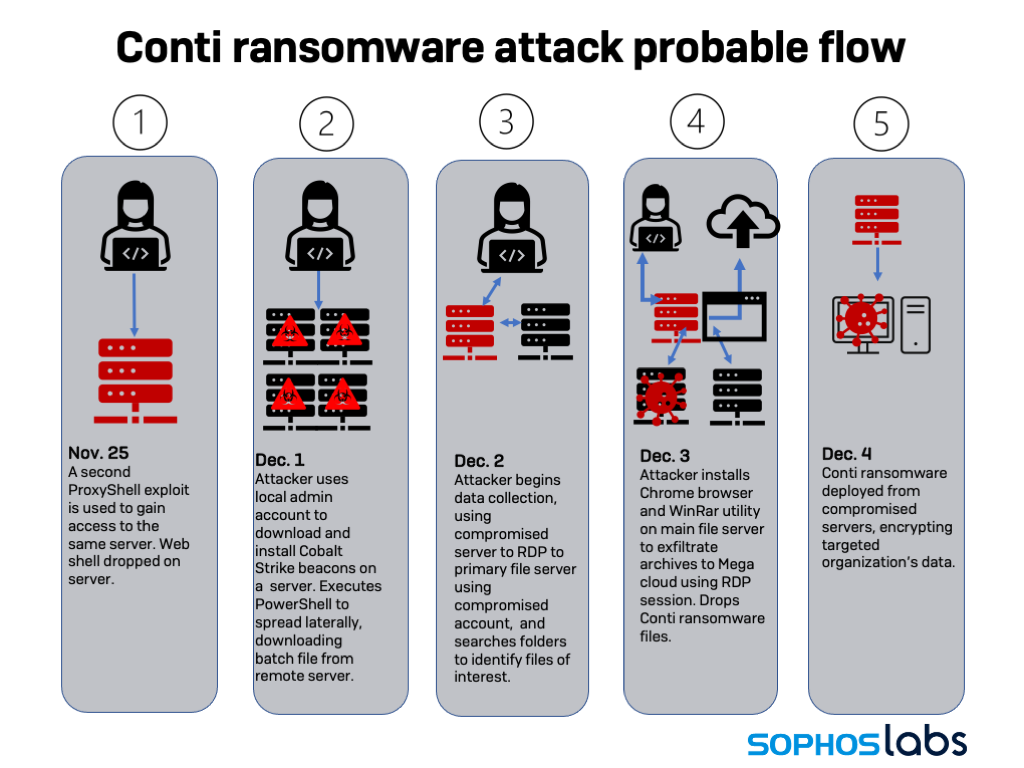
Conti and Karma actors attack healthcare provider at same time through ProxyShell exploits – Sophos News
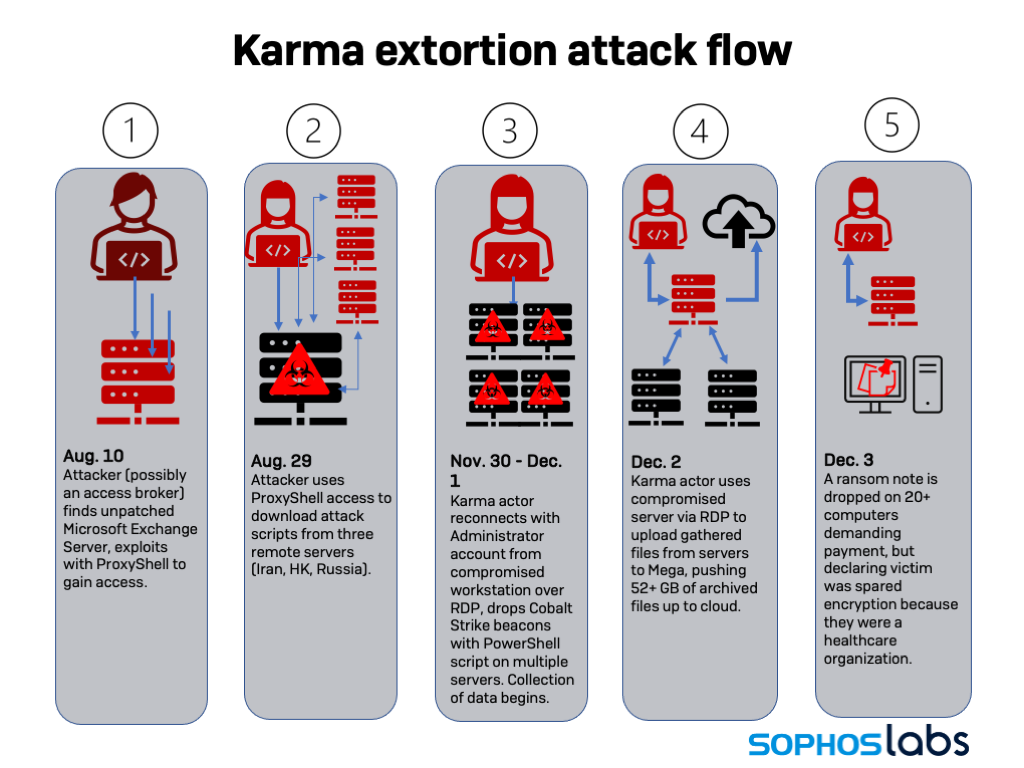
Conti and Karma actors attack healthcare provider at same time through ProxyShell exploits – Sophos News
GitHub - netero1010/RDPHijack-BOF: Cobalt Strike Beacon Object File (BOF) that uses WinStationConnect API to perform local/remote RDP session hijacking.